How Asymetric Public Private Key Pairs Are Generated
- How Asymmetric Public Private Key Pairs Are Generated Mean
- How Asymmetric Public Private Key Pairs Are Generated In California
- How Asymmetric Public Private Key Pairs Are Generated In Florida
- How Asymmetric Public Private Key Pairs Are Generated 2017
- How Asymmetric Public Private Key Pairs Are Generated In The World
Asymmetric keys, also known as public/private key pairs, are used for asymmetric encryption. Asymmetric encryption is used mainly to encrypt and decrypt session keys and digital signatures. Asymmetric encryption uses public key encryption algorithms.
For Those Looking for a Key. License key and region dont match, is it a us code? Original Poster 1 point 4 years ago. Action Replay Powersaves for the Nintendo 3DS Post here. Created Apr 3, 2014. Help Reddit App Reddit coins Reddit premium Reddit gifts. Action replay wii license key generator free. Wii Action Replay uses real cheat codes to get to the heart of your Nintendo Wii games, giving you enhancements such as Infinite Lives, Infinite Health, All Vehicles, All Levels and other exciting cheats. Wii Mac Address. Download Codelist EU. If you have lost your US license key for whatever reason; don't fret. Here's mine: 86A86BA02759FE17B1A79F. My email is sporty.tito@yahoo.com. I lost the password to that email so I don't even care. EDIT 12/22/14: The license key still works. Please make sure you are typing in the key correctly. I still don't know if the email matters.
Public key algorithms use two different keys: a public key and a private key. The private key member of the pair must be kept private and secure. The public key, however, can be distributed to anyone who requests it. The public key of a key pair is often distributed by means of a digital certificate. When one key of a key pair is used to encrypt a message, the other key from that pair is required to decrypt the message. Thus if user A's public key is used to encrypt data, only user A (or someone who has access to user A's private key) can decrypt the data. If user A's private key is used to encrypt a piece of data, only user A's public key will decrypt the data, thus indicating that user A (or someone with access to user A's private key) did the encryption.
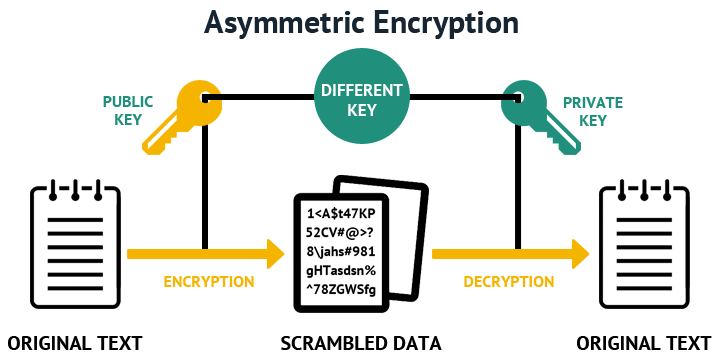
Public-key cryptography, or asymmetric cryptography, is a cryptographic system that uses pairs of keys: public keys which may be disseminated widely, and private keys which are known only to the owner. Generating unique public-private key pairs closed Consider that there 100 computers in a network where each computer is required to generate 10 unique public-private key pairs and that each of the 100 X 10 pairs are to be unique.
If the private key is used to sign a message, the public key from that pair must be used to validate the signature. For example, if Alice wants to send someone a digitally signed message, she would sign the message with her private key, and the other person could verify her signature by using her public key. Because presumably only Alice has access to her private key, the fact that the signature can be verified with Alice's public key indicates that Alice created the signature.
How Asymmetric Public Private Key Pairs Are Generated Mean

Unfortunately, public key algorithms are very slow, roughly 1,000 times slower than symmetric algorithms. It is impractical to use them to encrypt large amounts of data. In practice, public key algorithms are used to encrypt session keys. Symmetric algorithms are used for encryption/decryption of most data.
How Asymmetric Public Private Key Pairs Are Generated In California
Similarly, because signing a message, in effect, encrypts the message, it is not practical to use public key signature algorithms to sign large messages. Instead, a fixed-length hash is made of the message and the hash value is signed. For more information, see Hashes and Digital Signatures.
How Asymmetric Public Private Key Pairs Are Generated In Florida
Each user generally has two public/private key pairs. One key pair is used to encrypt session keys and the other to create digital signatures. These are known as the key exchange key pair and the signature key pair, respectively.
How Asymmetric Public Private Key Pairs Are Generated 2017
Note that although key containers created by most cryptographic service providers (CSPs) contain two key pairs, this is not required. Some CSPs do not store any key pairs while other CSPs store more than two pairs.
How Asymmetric Public Private Key Pairs Are Generated In The World
All keys in CryptoAPI are stored within CSPs. CSPs are also responsible for creating the keys, destroying them, and using them to perform a variety of cryptographic operations. Exporting keys out of the CSP so that they can be sent to other users is discussed in Cryptographic Key Storage and Exchange.